Get More From Your Technology
At work, at home, and everywhere in between, we all use technology to make life easier, or better. At Killbox, we complement your technology with advanced security features, logging and alerting capabilities, and an automation framework that requires no technical knowledge to operate. Simply put, by using your technology through a Killbox Integration, you get more.
*any technology that does not require physical access to operate can be integrated
Don't settle for prescribed integrations
Killbox Integration
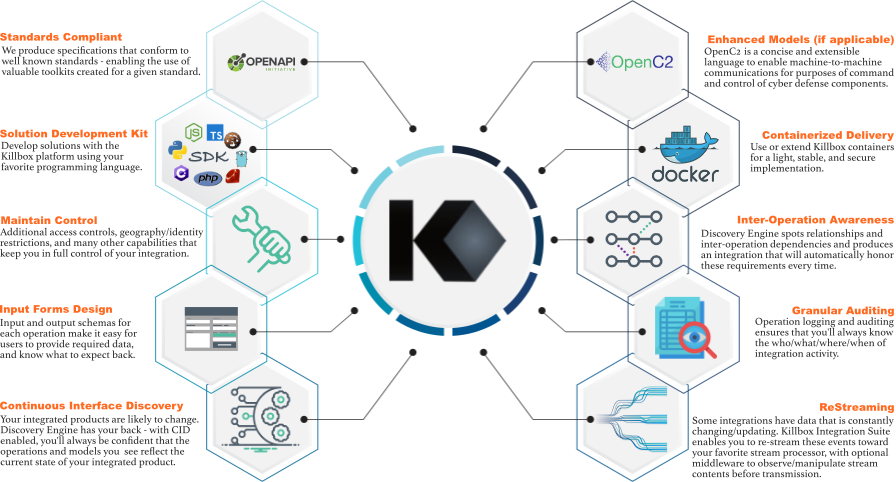
Scalable technology integration for business

Operating and maintaining a large number of technologies often means memorizing and accounting for the quirks of each one. Dozens of different ways to login, some browsers work while others don't, and having the ability to know when the service is degraded (or down) isn't always there. Killbox Dojo introduces consistency across your enterprise technologies:
- Authentication: SSO, AD, Contractor/Partner Access
- Authorization: RBAC, Time Restrictions, Source IP
- Accounting: Activity Logging, Status (Up/Down) Alerts, Event Alerts
Implementation for any use-case
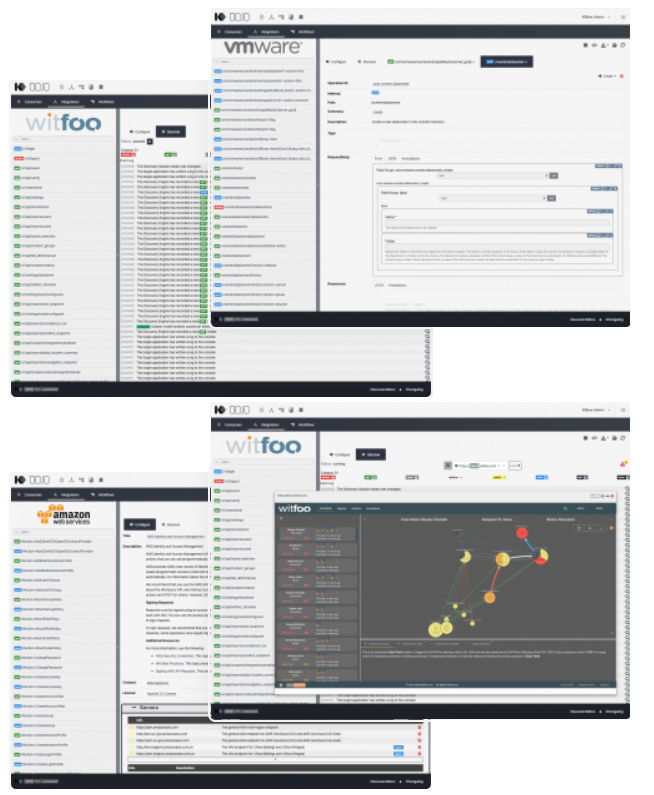
Integration Library
Many integration targets, such as Cloud Providers, SaaS Products, and pure APIs, are exposed to the world in the same way for everyone. We continuously update and maintain these integrations, and make them available to Killbox Integration Library subscribers.

Where it all started

Killbox Actual is an on-demand drop-in incident response server built to dramatically increase blue team speed and effectiveness during an active incident response.
- Your internal processes and procedures are ingrained throughout the system to ensure that the right people get involved in the right way, at the right time.
- Killbox Dojo's automation engine virtually eliminates common mistakes and typos and enables your team to respond at machine speed.
- All incident response activity and communication is logged so that teams can highlight their achievements and sharpen their skills.
- Secure and instant team communication tools are embedded into the interface built specifically for Incident Response
- Threat Origin Analysis occurs throughout the Incident Response period, so that you may proceed with confidence to patch your defenses afterward.
Powered By Killbox Discovery Engine
At the core of every Killbox product is our work on sustainable and consistent technology discovery without having to rely on another vendor's assistance or documentation. Our Discovery Engine can produce an integration package for any technology that does not require physical presence to manage.
We believe that the products you use every day can provide much more value, and that the path to significant value is through comprehensive integration.